

The toughest jobs need the tightest security
Security from end-to-end
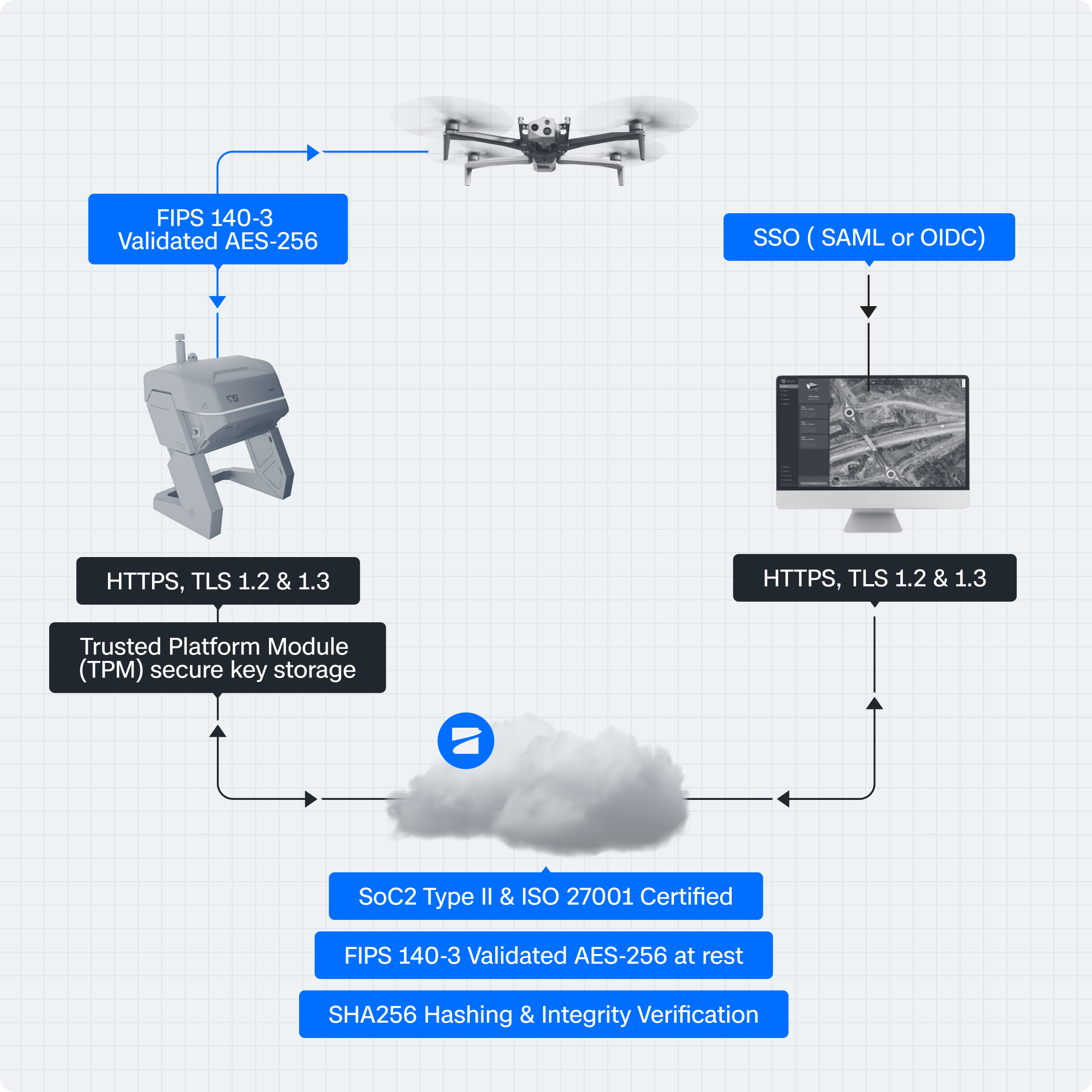
Skydio products are secure by design, safeguarding each layer of the UAS stack against external threats. From the way we source parts to the way we develop software, security is integrated from end-to-end to ensure the confidentiality, integrity, and availability of your data.
The most demanding organizations in the world trust Skydio because:
- FIPS 140-3 validated encryption protects data in transit and at rest.
- U.S.-based secure cloud with enterprise access controls — All customer data resides in the U.S. (AWS), with Single Sign On (SSO) support for SAML, OIDC, and Axon Connect.
- Evidence Integrity — Each capture is hashed with SHA256 at the point of capture and verified in Skydio Cloud, ensuring a courtroom-defensible chain of custody.
- Hardware-based key security — The Skydio Dock uses a Trusted Platform Module (TPM) to securely store encryption keys, meeting CJIS 6.0 key management requirements.
- Independent review & secure updates — Skydio’s CJIS workflows have been reviewed by a FedRamp-accredited 3PAO, and all firmware/software updates are digitally signed and verified before installation.
Hardware Security
Designed, assembled, and supported in the U.S
We work with manufacturing partners to prioritize security from the start, ensuring we protect our critical systems that store data from external threats.
Cloud
Hosted on secure infrastructure in the U.S.
We protect your data in transit and at rest within Skydio Cloud where our customers manage their fleet, sync media from flights, view and share live streams from current flights, and remotely control Skydio drones through teleoperation.
Compliance
Meeting the highest security standards
Skydio is committed to earning best-in-class security compliance certifications from industry-standard evaluators. Our customers can rest assured that their data is protected by security measures that meet or exceed the highest standards.

















